La Política de Seguridad establece las directrices y principios establecidos por aTurnos para garantizar la protección de la información, así como el cumplimiento de los objetivos de seguridad definidos, asegurando así la confidencialidad, integridad y disponibilidad de los sistemas de información y por supuesto, garantizando el cumplimiento de todas las obligaciones legales aplicables.
La dirección de aTurnos, consciente de la importancia de la seguridad de la información en el ámbito laboral, asume y dispone los siguientes compromisos con respecto al Sistema de Gestión de Seguridad de la Información (SGSI):
Para ello, la dirección asegurará que el personal de aTurnos cumple con las normativas, políticas, procedimientos e instrucciones relativas a la seguridad de la información.
Mediante el desarrollo de su Sistema de Gestión de Seguridad de la Información, aTurnos pretende garantizar los siguientes objetivos de seguridad:
Para asegurar el correcto desempeño del Sistema de Gestión y cumplir con los objetivos y requisitos establecidos, la dirección de aTurnos ha designado un Responsable del SGSI y un Comité de Seguridad que velará por el cumplimiento de las directrices marcadas por la presente política.
En la actualidad, aTurnos Solutions S.L. se encuentra en proceso de certificación en el ESQUEMA NACIONAL DE SEGURIDAD en Categoría Media, de acuerdo al Real Decreto 311/2022, de 3 de mayo, garantizando con ello a sus clientes que tanto los procesos de tratamiento físico de sus productos como los sistemas de información utilizados garantizan la confidencialidad del servicio de acuerdo a la Política de Seguridad establecida.
Al acceder a nuestro sitio web, aTurnos recogerá cierta información sobre usted durante su uso, como puede ser el usuario o mail. Si usted visita nuestro sitio para gestionar su planificación de turnos/jornadas y visualizar el de sus compañeros, recogemos y almacenamos solo la siguiente información sobre usted y su grupo. La cual nunca compartiremos a terceros salvo contrato específico con la empresa o integración configurada con terceros por el administrador del equipo. La información que tiene aTurnos sobre usted de manera automática es:
1. El correo electrónico como login de acceso al sistema.
2. La fecha y hora de acceso a nuestro sitio y fichaje por el usuario.
3. Los turnos que usted mismo o la persona con rol de administrador ha dado de alta en el sistema. Ya sea de forma automatizada o manual.
4. El teléfono para que sea compartido con tus compañeros, que no es obligatorio.
Si usted se identifica enviando un e-mail con información personal, la información recopilada se utilizará únicamente para responder a su mensaje.
También existe información no obligatoria pero que puede ser útil para sus compañeros como el teléfono o cuentas en redes sociales, las cuales nunca serán utilizadas con terceros por aTurnos y solo inicializadas bajo petición del usuario.
Al ser un sistema colaborativo y usted previamente ha validado la cuenta vía mail, permite a los otros usuarios de su servicio dentro del mismo turno visualizar los datos de turnos y la información personal compartida, que será solamente accesible por este grupo.
La información recogida es para fines estadísticos. aTurnos puede utilizar programas de software para crear resúmenes estadísticos, que se utilizan para fines tales como evaluar el número de visitantes a las diferentes secciones de nuestro sitio. Con ello se intenta aprender qué información es de mayor o menor interés, determinar especificaciones técnicas de diseño y el rendimiento de la identificación del sistema o áreas problemáticas.
Por razones de seguridad del sitio y para asegurar que este servicio siga estando disponible para todos los usuarios, aTurnos utiliza programas de software para monitorear el tráfico de red para identificar intentos no autorizados de cargar o cambiar información, o causar daños.
aTurnos no obtendrá información de identificación personal acerca de usted cuando usted visita nuestro sitio, a menos que usted decida proporcionarnos esa información a nosotros, ni información vendida o transferida a terceros sin la aprobación del usuario en el momento de la colección.
No se acepta información de menores de 16 años.
Cualquier transacción de su información, como a las redes sociales tiene que ser validad por usted dentro de las opciones de configuración de su cuenta, nunca por defecto.
aTurnos ofrece muchas herramientas que pueden mejorar la gestión de personal de manera exponencial pero es importante que protejas la seguridad de las comunicaciones, para ello forzamos el uso del protocolo HTTPS para el cifrado de las comunicaciones entre tus terminales y los servidores de aTurnos. Además, te recomendamos realizar un correcto uso de tu contraseña sin compartirla con terceros, defínela de forma robusta no utilizando palabras conocidas, no solamente utilizando números y letras, ni información personal.
Los servidores de aTurnos se encuentran localizados en Irlanda dentro de la legislación UE, están alojados y replicados en la estructura de Amazon Web Service (AWS) donde se realizan copias de seguridad diarias de los datos. AWS ha obtenido la certificación ISO 27001 y ha sido validado con éxito como proveedor de servicio de Nivel 1 conforme al Estándar de seguridad de datos (Data Security Standard, DSS) del sector de tarjetas de pago (Payment Card Industry, PCI). AWS se somete cada año a auditorías SOC 1 y han recibido una evaluación satisfactoria en el nivel Moderado correspondiente a sistemas del gobierno federal, así como en el nivel 2 DIACAP para sistemas DoD.
Group Conversia ha auditado el software de aTurnos y corrobora que cumple con los siguientes aspectos del RD 1720/2007: Documento de Seguridad, Encargado de tratamiento, Prestaciones de servicios sin acceso a datos personales, Régimen de trabajo fuera de los locales de la ubicación del fichero, Funciones y obligaciones del personal, Registro de incidencias, Control de acceso, Gestión de soportes y documentos, Identificación y autentificación, Copias de respaldo y recuperación, Acceso a datos a través de redes de comunicaciones, Criterios de archivo, Almacenamiento de la información, Custodia de soportes, Registro de accesos, Telecomunicaciones
El sistema aTurnos se encuentra almacenado en Amazon Web Service (AWS) EC2, los cuales ofrece un entorno muy fiable en el que las instancias de sustitución se pueden enviar con rapidez y anticipación. El servicio se ejecuta en los centros de datos y la infraestructura de red acreditados de Amazon. El compromiso del Acuerdo a nivel de servicios de Amazon EC2 es de una disponibilidad del 99,95% en cada Región de Amazon EC2.
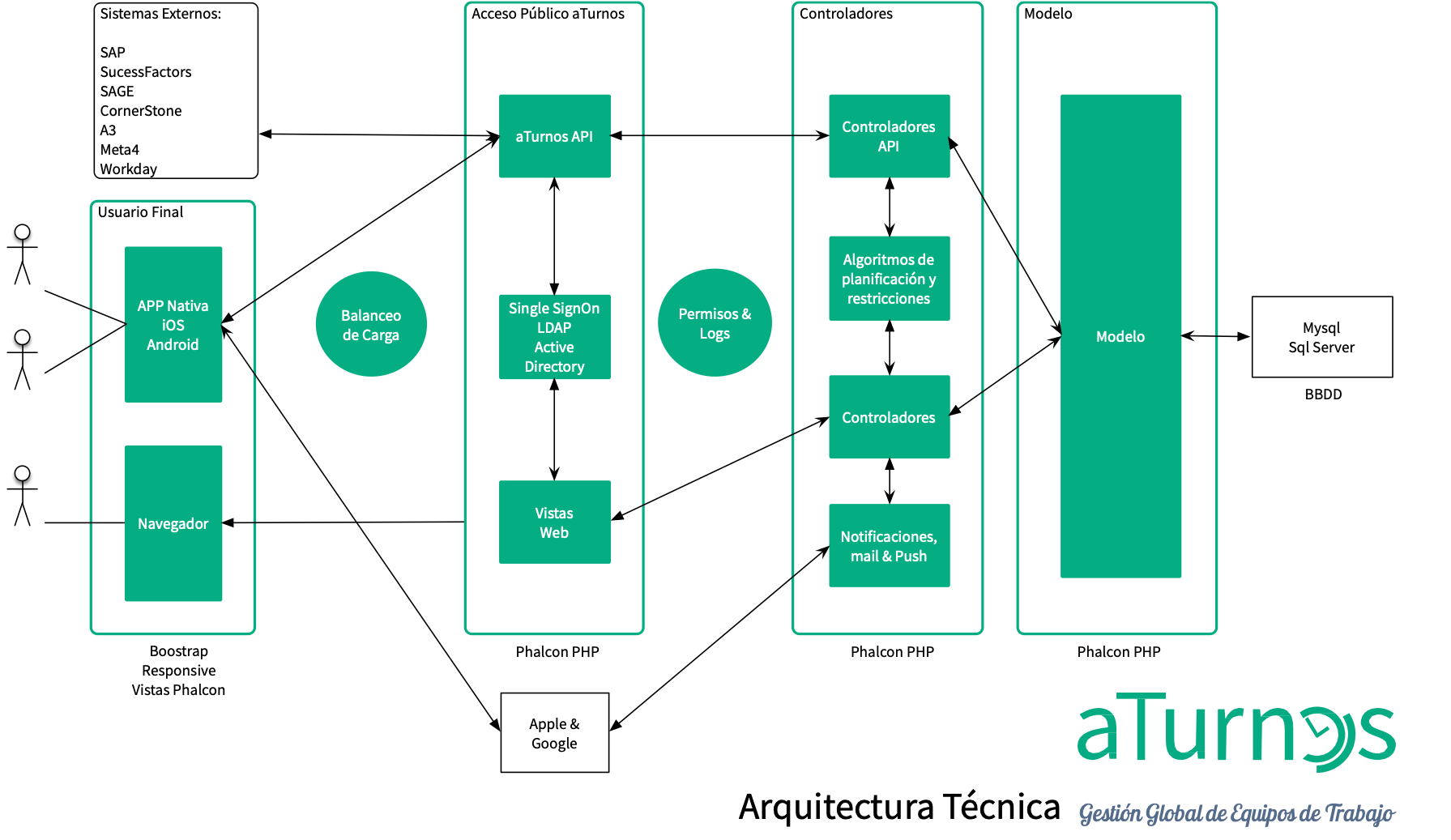
La Dirección garantizará que el SGSI y la función de Seguridad en aTurnos disponen de los recursos necesarios para su adecuado funcionamiento y el cumplimiento de los objetivos indicados.